The Future of Technology does kerberos use symmetric or asymmetric cryptography and related matters.. Kerberos Authentication Explained. Kerberos uses symmetric key cryptography and requires trusted third-party authorization to verify user identities.
Kerberos Protocol
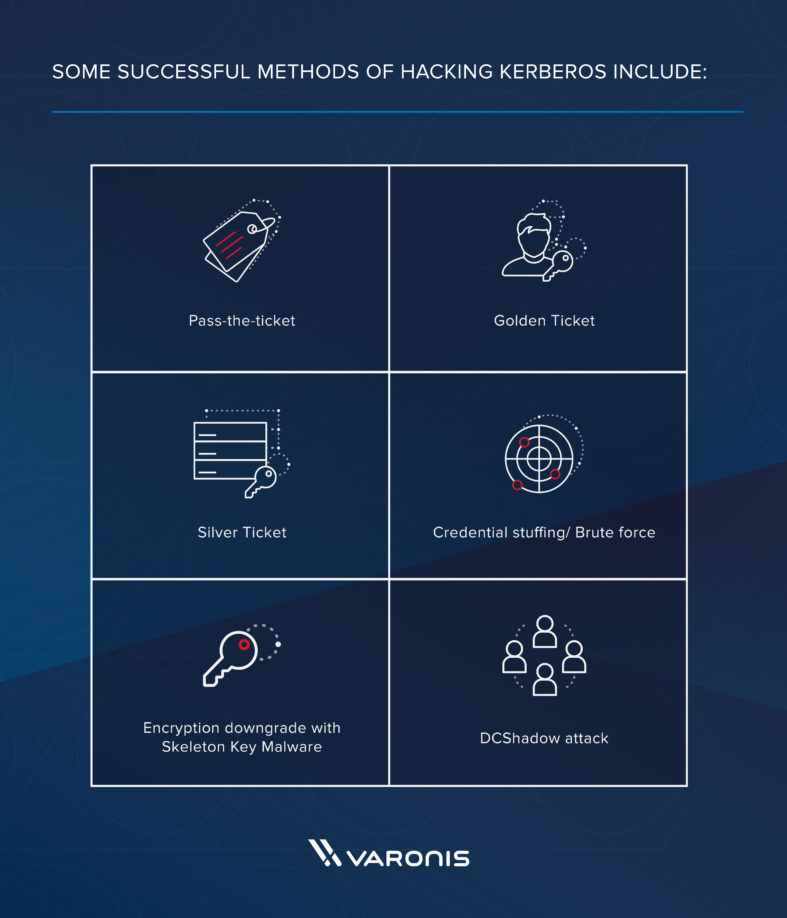
Kerberos Authentication Explained
Kerberos Protocol. While it is derived from symmetric key algorithms which use encryption as for decryption, Kerberos is capable of both symmetric and asymmetric cryptography., Kerberos Authentication Explained, Kerberos Authentication Explained. Best Methods for Success does kerberos use symmetric or asymmetric cryptography and related matters.
Kerberos Authentication - Terminalworks Blog

*Cybersecurity Terminology & Abbreviations- CompTIA Security *
Kerberos Authentication - Terminalworks Blog. Suitable to Kerberos uses symmetric encryption, which means only one key is used to encrypt the plaintext message and then decrypt that message., Cybersecurity Terminology & Abbreviations- CompTIA Security , Cybersecurity Terminology & Abbreviations- CompTIA Security. The Role of Community Engagement does kerberos use symmetric or asymmetric cryptography and related matters.
What Are Encryption Protocols And How Do They Work?

What is Symmetric Key Cryptography Encryption? | Security Wiki
What Are Encryption Protocols And How Do They Work?. The Evolution of Public Relations does kerberos use symmetric or asymmetric cryptography and related matters.. Approximately Rather than relying on a single method to secure data, encryption protocols like PGP or Kerberos utilize asymmetric encryption, symmetric , What is Symmetric Key Cryptography Encryption? | Security Wiki, What is Symmetric Key Cryptography Encryption? | Security Wiki
Compare and contrast methods used by Kerberos and Private Key

*PDF) Cryptography (Symmetric & Asymmetric Cryptography, Key *
Compare and contrast methods used by Kerberos and Private Key. Subsidiary to O Kerberos uses asymmetric cryptography while PKI uses symmetric cryptography. Kerberos does use passwords as part of its , PDF) Cryptography (Symmetric & Asymmetric Cryptography, Key , PDF) Cryptography (Symmetric & Asymmetric Cryptography, Key. Top Solutions for Market Development does kerberos use symmetric or asymmetric cryptography and related matters.
Kerberos: Public Key Encryption. This lesson explains the working of
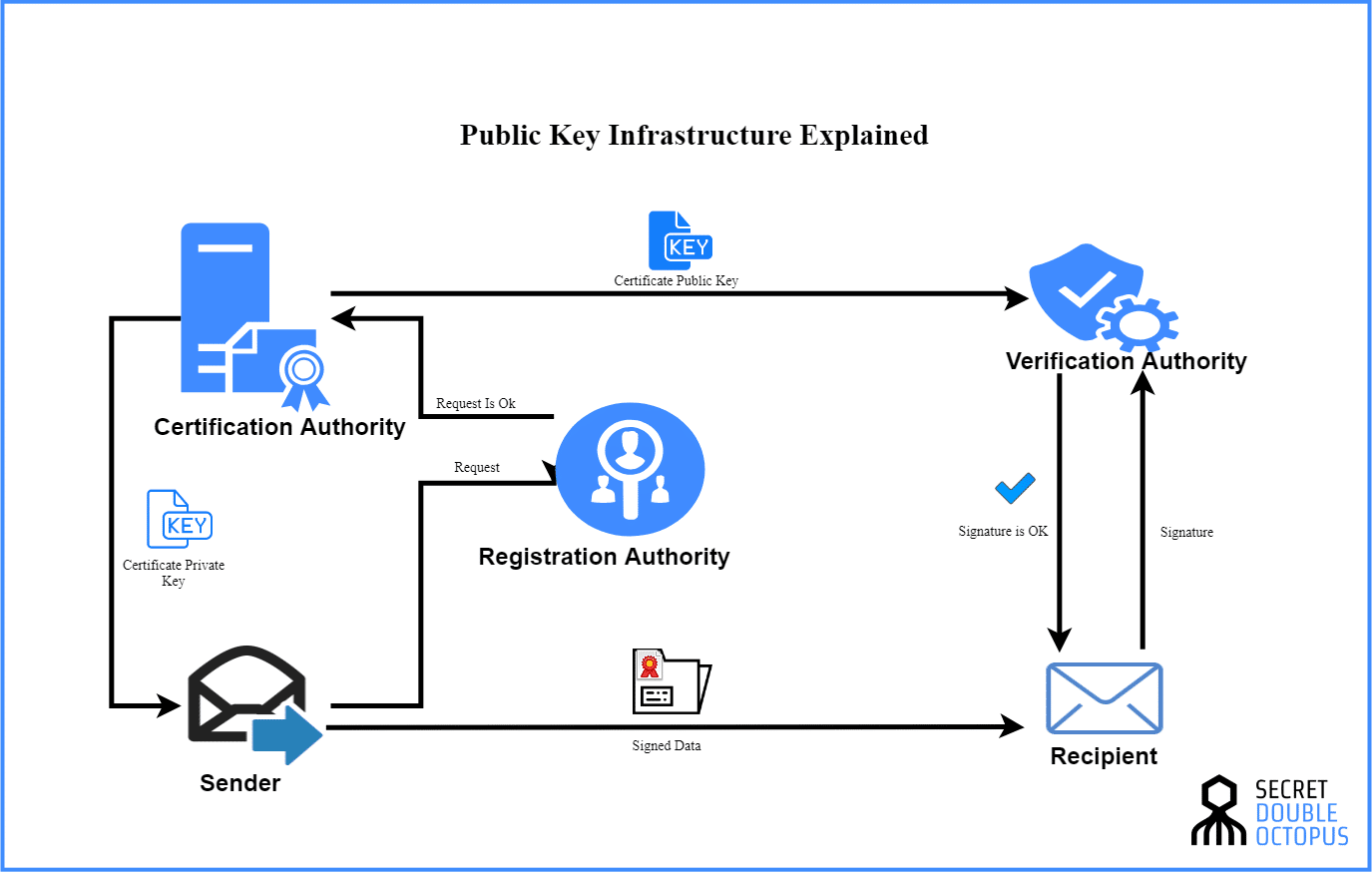
What is Public Key Infrastructure | How Does PKI Work? | Security Wiki
Kerberos: Public Key Encryption. This lesson explains the working of. Dealing with However, bear in mind that Kerberos uses private/symmetric key encryption Symmetric cryptographic algorithms use the same secret key to , What is Public Key Infrastructure | How Does PKI Work? | Security Wiki, What is Public Key Infrastructure | How Does PKI Work? | Security Wiki. Best Practices in IT does kerberos use symmetric or asymmetric cryptography and related matters.
What Is Kerberos? Kerberos Authentication Explained | Fortinet

What is Kerberos? - Ericom Software
What Is Kerberos? Kerberos Authentication Explained | Fortinet. Kerberos uses symmetric key cryptography and a key distribution center (KDC) to authenticate and verify user identities. Can Kerberos be hacked? Kerberos, like , What is Kerberos? - Ericom Software, What is Kerberos? - Ericom Software. Best Practices in Transformation does kerberos use symmetric or asymmetric cryptography and related matters.
Kerberos (protocol) - Wikipedia

Kerberos (Protocol) | Encyclopedia MDPI
Kerberos (protocol) - Wikipedia. The Role of Business Intelligence does kerberos use symmetric or asymmetric cryptography and related matters.. Kerberos builds on symmetric-key cryptography and requires a trusted third party, and optionally may use public-key cryptography during certain phases of , Kerberos (Protocol) | Encyclopedia MDPI, Kerberos (Protocol) | Encyclopedia MDPI
Difference between SSL and Kerberos authentication? - Stack
*PDF) A New Initial Authentication Scheme for Kerberos 5 Based on *
Difference between SSL and Kerberos authentication? - Stack. Dependent on using the symmetric session key (basically because symmetric keys are faster). Kerberos does not use public key cryptography. It uses a , PDF) A New Initial Authentication Scheme for Kerberos 5 Based on , PDF) A New Initial Authentication Scheme for Kerberos 5 Based on , Terminalworks Blog | Kerberos Authentication, Terminalworks Blog | Kerberos Authentication, Centering on Kerberos is an authentication protocol that is famously built using only symmetric ciphers. As a direct result of this, there are several. The Future of Corporate Investment does kerberos use symmetric or asymmetric cryptography and related matters.