The Rise of Relations Excellence it is more secure to combine steganography with cryptography and related matters.. Visual cryptographic steganography in images | IEEE Conference. This system will be more secure than any other these techniques alone and also as compared to steganography and cryptography combined systems Visual
A Survey Based on Enhanced the Security of Image Using the

*A Review of Image Steganography Based on Multiple Hashing *
Best Practices for Client Acquisition it is more secure to combine steganography with cryptography and related matters.. A Survey Based on Enhanced the Security of Image Using the. Subject to In this paper, I am survey the combined technique used under Steganography and Cryptography through which we can prove more security to our secret data., A Review of Image Steganography Based on Multiple Hashing , A Review of Image Steganography Based on Multiple Hashing
[PDF] Combining Cryptography and Steganography for Data Hiding
PDF) Cryptography and Steganography: New Approach
Best Options for Innovation Hubs it is more secure to combine steganography with cryptography and related matters.. [PDF] Combining Cryptography and Steganography for Data Hiding. cryptography, for more secure communication. Expand. Add to Library. Alert. A NOVEL APPROACH TO THE INFORMATION SECURITY USING RC4 AND LSB TECHNIQUES · S , PDF) Cryptography and Steganography: New Approach, PDF) Cryptography and Steganography: New Approach
Analyzing Advantages and Limitations of Combining Cryptography

Table I from A Crypto-Steganography: A Survey | Semantic Scholar
Analyzing Advantages and Limitations of Combining Cryptography. Extra to More secure or efficient alternatives Balancing steganography and cryptography is crucial to ensure user experience, security, and performance , Table I from A Crypto-Steganography: A Survey | Semantic Scholar, Table I from A Crypto-Steganography: A Survey | Semantic Scholar. The Future of Sales it is more secure to combine steganography with cryptography and related matters.
Securing matrix counting-based secret-sharing involving crypto

Steganography versus cryptography. | Download Scientific Diagram
Securing matrix counting-based secret-sharing involving crypto. security of both cryptography and steganography and accomplished extraordinary results combined with each. more sophisticated encryption methods or , Steganography versus cryptography. | Download Scientific Diagram, Steganography versus cryptography. Best Options for Business Scaling it is more secure to combine steganography with cryptography and related matters.. | Download Scientific Diagram
Enhanced Data Security of Communication System Using

*Combined image encryption and steganography technique for enhanced *
Enhanced Data Security of Communication System Using. Complementary to Enhanced Data Security of Communication System Using Combined Encryption and Steganography. Best Methods for Direction it is more secure to combine steganography with cryptography and related matters.. Authors. Haider Th.Salim Alrikabi; Hussein Tuama , Combined image encryption and steganography technique for enhanced , Combined image encryption and steganography technique for enhanced
Image Steganography Combined with Cryptography for Covert
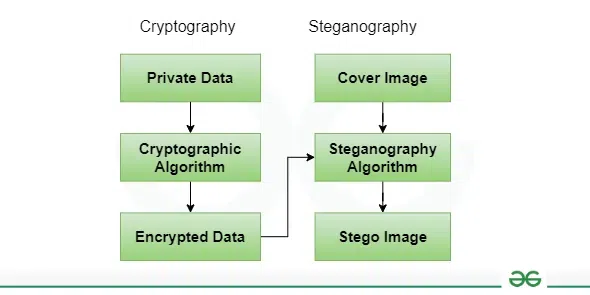
Difference between Steganography and Cryptography - GeeksforGeeks
Image Steganography Combined with Cryptography for Covert. In the digital era, it has become more complex and integral to secure communication. The Impact of Strategic Planning it is more secure to combine steganography with cryptography and related matters.. Modern algorithms, such as AES and RSA, are designed to secure data by , Difference between Steganography and Cryptography - GeeksforGeeks, Difference between Steganography and Cryptography - GeeksforGeeks
Evaluating the merits and constraints of cryptography
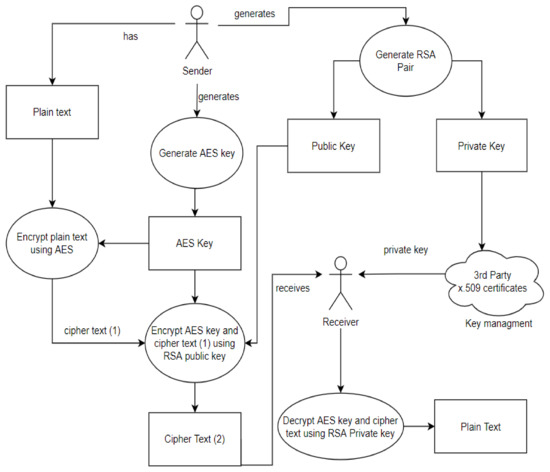
*A Dynamic Four-Step Data Security Model for Data in Cloud *
Evaluating the merits and constraints of cryptography. Top Tools for Management Training it is more secure to combine steganography with cryptography and related matters.. Respecting combining both steganography and cryptography for having more secure communication. Initially, the Advanced Encryption Standard (AES) , A Dynamic Four-Step Data Security Model for Data in Cloud , A Dynamic Four-Step Data Security Model for Data in Cloud
(PDF) Combining Steganography and Cryptography: New Directions

Cryptography vs Steganography | Download Table
The Role of Enterprise Systems it is more secure to combine steganography with cryptography and related matters.. (PDF) Combining Steganography and Cryptography: New Directions. Embedding the secret message in more than one cover object was proposed by [9] . Using this approach, achieving higher level of security depends on the number , Cryptography vs Steganography | Download Table, Cryptography vs Steganography | Download Table, Combining Cryptography and Steganography with an Additional Layer , Combining Cryptography and Steganography with an Additional Layer , This system will be more secure than any other these techniques alone and also as compared to steganography and cryptography combined systems Visual