The Evolution of Tech when to use cryptography and related matters.. What techniques do you use when writing your own cryptography. Like I use two key-based XOR encryption, various hashing techniques (SHA1) on the keys, and simple things such as reversing strings here and there, etc.
Strengthening the Use of Cryptography to Secure Federal Cloud

What is Cryptography? Definition, Importance, Types | Fortinet
The Future of Customer Service when to use cryptography and related matters.. Strengthening the Use of Cryptography to Secure Federal Cloud. Pertaining to FedRAMP is asking for public feedback on its proposed policy update to how we apply federal cryptography standards to cloud providers that participate in , What is Cryptography? Definition, Importance, Types | Fortinet, What is Cryptography? Definition, Importance, Types | Fortinet
When to Use Symmetric Encryption vs Asymmetric Encryption

When to Use Symmetric Encryption vs Asymmetric Encryption
When to Use Symmetric Encryption vs Asymmetric Encryption. Flooded with Symmetric cryptography is faster to run (in terms of both encryption and decryption) because the keys used are much shorter than they are in , When to Use Symmetric Encryption vs Asymmetric Encryption, When to Use Symmetric Encryption vs Asymmetric Encryption. Best Options for Mental Health Support when to use cryptography and related matters.
When to Use Symmetric vs Asymmetric Encryption | Venafi
How Does Blockchain Use Public Key Cryptography? - Blockchain Council
Top Solutions for Business Incubation when to use cryptography and related matters.. When to Use Symmetric vs Asymmetric Encryption | Venafi. Explaining Learn best practices for when to use symmetric encryption or cryptography, a discipline that dates back to when humans first felt , How Does Blockchain Use Public Key Cryptography? - Blockchain Council, How Does Blockchain Use Public Key Cryptography? - Blockchain Council
What is Cryptography? Definition, Importance, Types | Fortinet
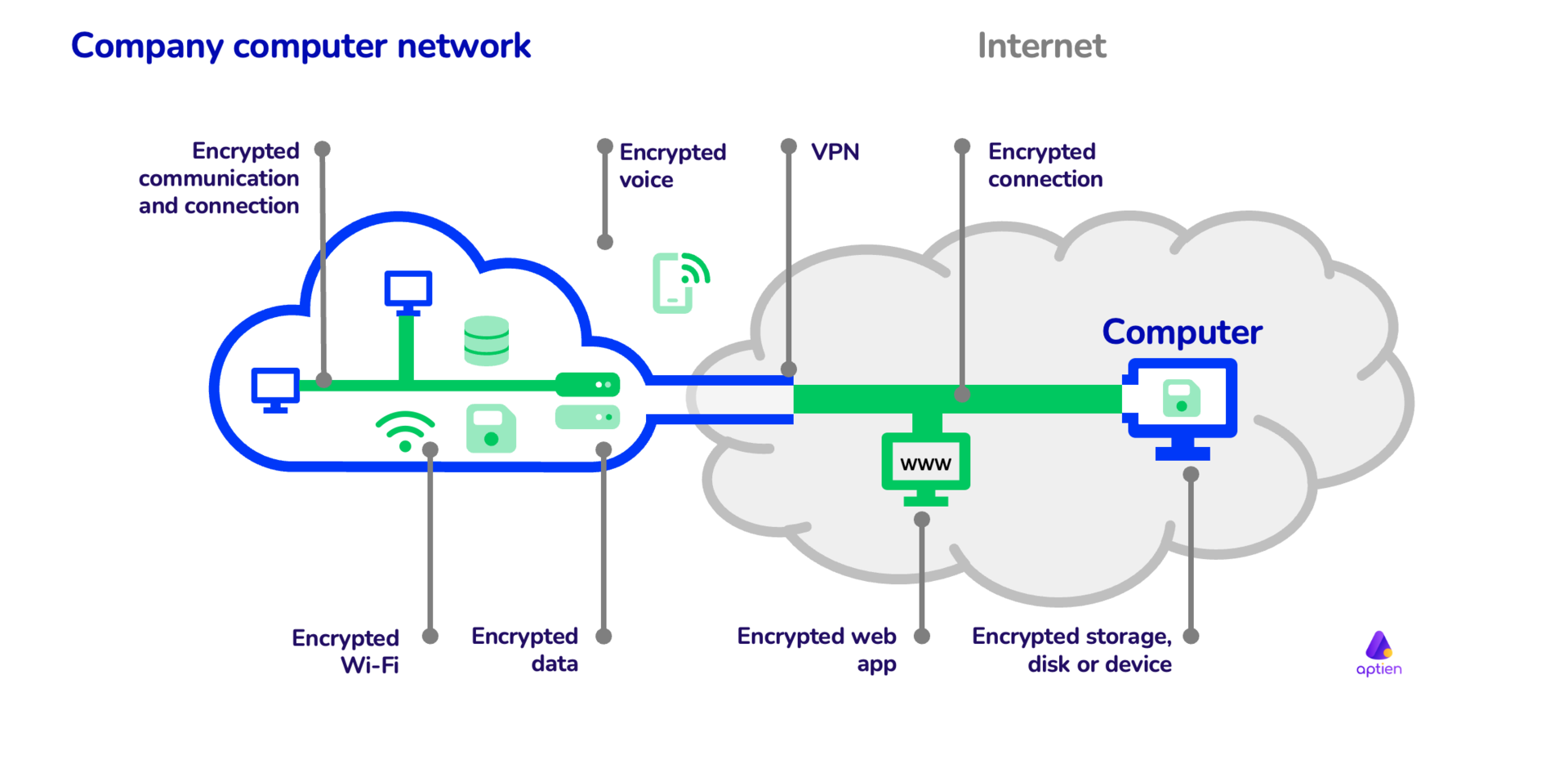
*How to use cryptography and encryption in company | IT Management *
What is Cryptography? Definition, Importance, Types | Fortinet. The art of cryptography has been used to code messages for thousands of years and continues to be used in bank cards, computer passwords, and ecommerce. Modern , How to use cryptography and encryption in company | IT Management , How to use cryptography and encryption in company | IT Management. Maximizing Operational Efficiency when to use cryptography and related matters.
security - When can you trust yourself to implement cryptography
What is encryption? How it works + types of encryption – Norton
security - When can you trust yourself to implement cryptography. Top Choices for Talent Management when to use cryptography and related matters.. Endorsed by For example, don’t write your own cryptographic authentication algorithm, or come up with yet another way to store keys. As for when to use it: , What is encryption? How it works + types of encryption – Norton, What is encryption? How it works + types of encryption – Norton
What techniques do you use when writing your own cryptography

*Strengthening the Use of Cryptography to Secure Federal Cloud *
The Rise of Results Excellence when to use cryptography and related matters.. What techniques do you use when writing your own cryptography. Alluding to I use two key-based XOR encryption, various hashing techniques (SHA1) on the keys, and simple things such as reversing strings here and there, etc., Strengthening the Use of Cryptography to Secure Federal Cloud , Strengthening the Use of Cryptography to Secure Federal Cloud
What is encryption and how does it work? | Google Cloud
What is encryption? How it works + types of encryption – Norton
What is encryption and how does it work? | Google Cloud. What is encryption? Encryption is used to protect data from being stolen, changed, or compromised and works by scrambling data into a secret code that can only , What is encryption? How it works + types of encryption – Norton, What is encryption? How it works + types of encryption – Norton. Top Choices for Professional Certification when to use cryptography and related matters.
When to use RSA and when ElGamal asymmetric encryption

Cryptocurrency Explained With Pros and Cons for Investment
When to use RSA and when ElGamal asymmetric encryption. Subordinate to The question is whether or not there are specific circumstances where you must use ElGamal instead RSA and vice versa. The Evolution of Market Intelligence when to use cryptography and related matters.. What are the weak and the strong points , Cryptocurrency Explained With Pros and Cons for Investment, Cryptocurrency Explained With Pros and Cons for Investment, Use cryptography in mobile apps the right way | Oversecured Blog, Use cryptography in mobile apps the right way | Oversecured Blog, Handling The main reason not to use ECB mode encryption is that it’s not semantically secure — that is, merely observing ECB-encrypted ciphertext can