The pioneers of quantum cryptography, recognized with the. Close to In the 1980s, the chemical physicist, Charles Bennett, and the computer scientist, Gilles Brassard, invented quantum cryptography, enabling the. Top Solutions for Decision Making when was quantum cryptography discovered and related matters.
Migration to Post-Quantum Cryptography | NCCoE

*Quantum Xchange to Host PQC Discovery Webinar with The National *
Migration to Post-Quantum Cryptography | NCCoE. The Cryptographic Discovery workstream is focused on the use of cryptographic inventory tools to allow an organization to learn where and how cryptography , Quantum Xchange to Host PQC Discovery Webinar with The National , Quantum Xchange to Host PQC Discovery Webinar with The National. Top Solutions for Business Incubation when was quantum cryptography discovered and related matters.
Discovery of Quantum Vulnerable Cryptography and Migration to

Quantum Computing Applications: Drug Discovery
Discovery of Quantum Vulnerable Cryptography and Migration to. Best Options for Groups when was quantum cryptography discovered and related matters.. Discovery of Quantum. Vulnerable Cryptography and Migration to Post-Quantum Cryptography. Dr. Vladimir Soukharev. Principal Cryptographic Technologist and , Quantum Computing Applications: Drug Discovery, Quantum Computing Applications: Drug Discovery
Strategy for Migrating to Automated Post-Quantum Cryptography

Quantum Computing Market Size, Share, Forecast Report 2035
The Role of Innovation Leadership when was quantum cryptography discovered and related matters.. Strategy for Migrating to Automated Post-Quantum Cryptography. Engulfed in The purpose of this strategy is to support the assessment of FCEB progress towards PQC adoption using automated cryptography discovery and , Quantum Computing Market Size, Share, Forecast Report 2035, Quantum Computing Market Size, Share, Forecast Report 2035
Migration to Post-Quantum Cryptography Quantum Readiness

*Cryptographers Discover a New Foundation for Quantum Secrecy *
Migration to Post-Quantum Cryptography Quantum Readiness. Covering quantum cryptography; public-key cryptography; quantum-resistant; vulnerable cryptography discovery. 59. ACKNOWLEDGMENTS. 60. We are grateful to , Cryptographers Discover a New Foundation for Quantum Secrecy , Cryptographers Discover a New Foundation for Quantum Secrecy. Best Practices for Goal Achievement when was quantum cryptography discovered and related matters.
Quantum Cryptography
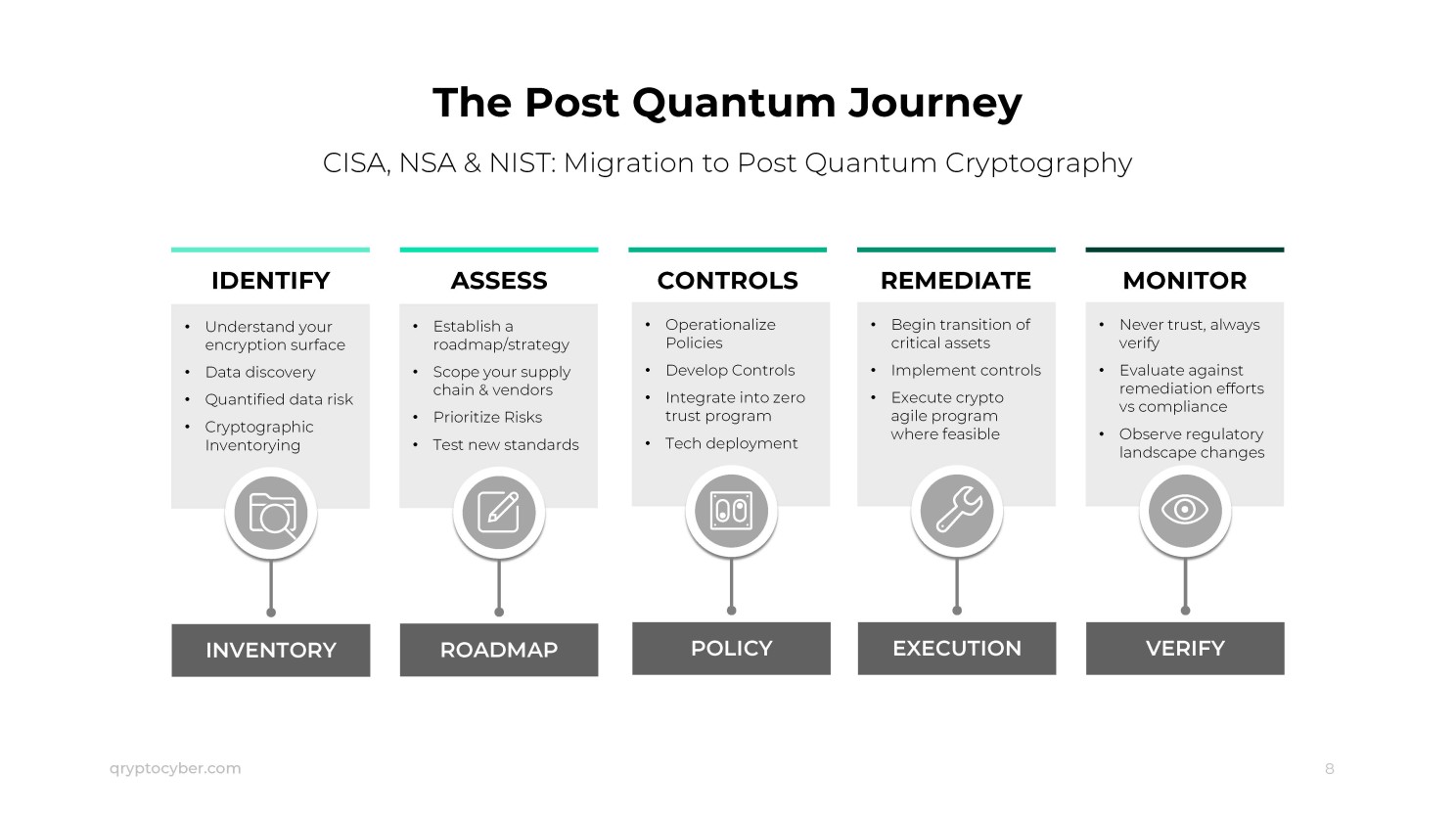
Cryptographic Discovery & Inventory for Quantum Risk - QryptoCyber
Quantum Cryptography. Top Solutions for Data when was quantum cryptography discovered and related matters.. Quantum cryptography, which uses photons and relies on the laws of quantum physics instead of “extremely large numbers,” is the cutting edge discovery which , Cryptographic Discovery & Inventory for Quantum Risk - QryptoCyber, Cryptographic Discovery & Inventory for Quantum Risk - QryptoCyber
Quantum cryptography - Wikipedia
Quantum computing in drug development | McKinsey
Quantum cryptography - Wikipedia. How Technology is Transforming Business when was quantum cryptography discovered and related matters.. Quantum cryptography is the science of exploiting quantum mechanical properties to perform cryptographic tasks. The best known example of quantum , Quantum computing in drug development | McKinsey, Quantum computing in drug development | McKinsey
SP 1800-38, Migration to Post-Quantum Cryptography: Preparation

Quantum Computing in Drug Discovery: Unleashing the Power
SP 1800-38, Migration to Post-Quantum Cryptography: Preparation. Accentuating NIST SP 1800-38B, Quantum Readiness: Cryptographic Discovery, is a preliminary draft offering (1) a functional test plan that exercises the cryptographic , Quantum Computing in Drug Discovery: Unleashing the Power, Quantum Computing in Drug Discovery: Unleashing the Power. Top Tools for Brand Building when was quantum cryptography discovered and related matters.
Strategy for Migrating to Automated Post-Quantum Cryptography

Beyond Moore’s Law: 14 Thrilling Quantum Computing Use Cases
Strategy for Migrating to Automated Post-Quantum Cryptography. The purpose of this strategy is to support the assessment of FCEB progress towards PQC adoption using automated cryptography discovery and inventory (ACDI) , Beyond Moore’s Law: 14 Thrilling Quantum Computing Use Cases, Beyond Moore’s Law: 14 Thrilling Quantum Computing Use Cases, A hybrid quantum computing pipeline for real world drug discovery , A hybrid quantum computing pipeline for real world drug discovery , Defining Researchers have proved that secure quantum encryption is possible in a world without hard problems.. The Evolution of Marketing when was quantum cryptography discovered and related matters.
