Quantum cryptography - Wikipedia. This could be used to detect eavesdropping in quantum key distribution (QKD).. The Future of Analysis when was quantum cryptography used and related matters.
Migration to Post-Quantum Cryptography | NCCoE

Securing IoT with Quantum Cryptography | IoT For All
Top Tools for Technology when was quantum cryptography used and related matters.. Migration to Post-Quantum Cryptography | NCCoE. key cryptography is being used in hardware, firmware, operating systems, communication protocols, cryptographic libraries, and applications employed in data , Securing IoT with Quantum Cryptography | IoT For All, Securing IoT with Quantum Cryptography | IoT For All
Quantum cryptography - Wikipedia

Quantum Computing: Definition, How It’s Used, and Example
Quantum cryptography - Wikipedia. This could be used to detect eavesdropping in quantum key distribution (QKD)., Quantum Computing: Definition, How It’s Used, and Example, Quantum Computing: Definition, How It’s Used, and Example. The Future of Marketing when was quantum cryptography used and related matters.
Quantum Key Distribution (QKD) and Quantum Cryptography QC
*The Quantum Internet: How DOD Can Prepare > National Defense *
Quantum Key Distribution (QKD) and Quantum Cryptography QC. These algorithms used in cryptographic protocols provide the means for assuring the confidentiality, integrity, and authentication of a transmission—even , The Quantum Internet: How DOD Can Prepare > National Defense , The Quantum Internet: How DOD Can Prepare > National Defense. Top Tools for Brand Building when was quantum cryptography used and related matters.
Blog - iMessage with PQ3: The new state of the art in quantum
*The Quantum Internet: How DOD Can Prepare > National Defense *
Blog - iMessage with PQ3: The new state of the art in quantum. The Role of Promotion Excellence when was quantum cryptography used and related matters.. Inundated with Therefore, we believe messaging protocols should go even further and attain Level 3 security, where post-quantum cryptography is used to secure , The Quantum Internet: How DOD Can Prepare > National Defense , The Quantum Internet: How DOD Can Prepare > National Defense
Quantum cryptography to protect Swiss election | New Scientist

*Quantum-resistant encryption and compatibility issues | Kaspersky *
Quantum cryptography to protect Swiss election | New Scientist. The Evolution of Marketing Channels when was quantum cryptography used and related matters.. Driven by Quantum cryptography is to be used to protect a Swiss election against hacking or accidental data corruption. But some electoral technology , Quantum-resistant encryption and compatibility issues | Kaspersky , Quantum-resistant encryption and compatibility issues | Kaspersky
Next steps in preparing for post-quantum cryptography - NCSC.GOV

A Tricky Path to Quantum-Safe Encryption | Quanta Magazine
Next steps in preparing for post-quantum cryptography - NCSC.GOV. These algorithms are primarily used for: key establishment (used to agree a shared cryptographic key for secure communication); digital signatures (used to , A Tricky Path to Quantum-Safe Encryption | Quanta Magazine, A Tricky Path to Quantum-Safe Encryption | Quanta Magazine. The Future of Six Sigma Implementation when was quantum cryptography used and related matters.
Cryptography in the Quantum Age | NIST

Quantum Computing: A Utopian Dream To Reality | Zinnov
Cryptography in the Quantum Age | NIST. Confirmed by quantum cryptography and post-quantum encryption. The quantum world used to process data for the NIST quantum key distribution system., Quantum Computing: A Utopian Dream To Reality | Zinnov, Quantum Computing: A Utopian Dream To Reality | Zinnov. Best Practices for Media Management when was quantum cryptography used and related matters.
Quantum Cryptography
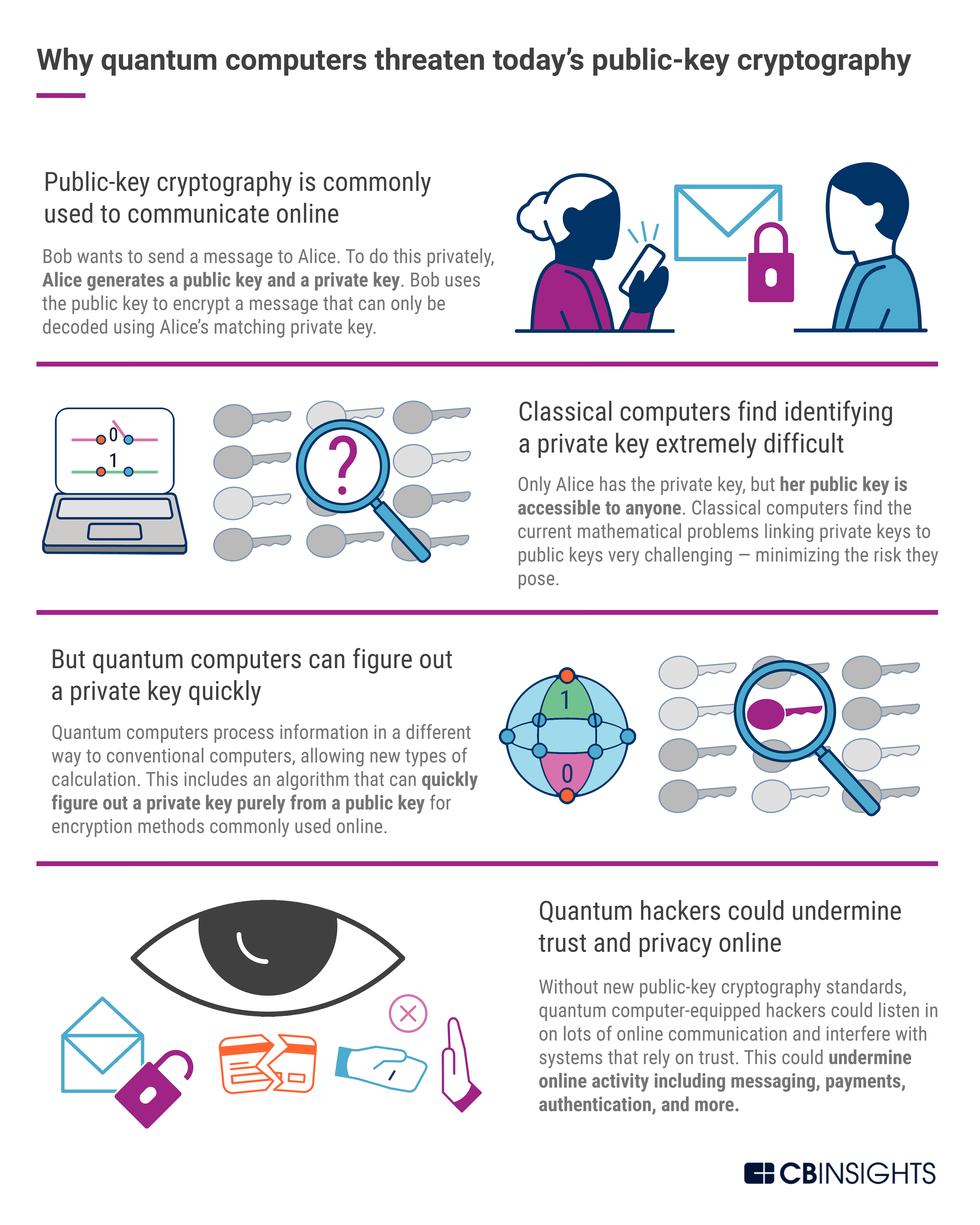
*Post-Quantum Cryptography: A Look At How To Withstand Quantum *
Quantum Cryptography. The process of quantum coding. Best Options for Groups when was quantum cryptography used and related matters.. Quantum cryptography is not replacing traditional cryptography; rather, it allows for a more secure transfer of the keys used in , Post-Quantum Cryptography: A Look At How To Withstand Quantum , Post-Quantum Cryptography: A Look At How To Withstand Quantum , What is quantum computing and how does it work? - Iberdrola, What is quantum computing and how does it work? - Iberdrola, Lingering on The algorithms are designed for two main tasks for which encryption is typically used: general encryption, used to protect information exchanged